# Secure keyboards
Many Weixin Mini Program businesses require the input of sensitive information, such as passwords, ID cards, phone numbers, etc. The unprofessional practice is to submit plain text to the back office of the business, which is very easy to leak in network transmission and does not meet compliance requirements. There are also improvements in the use of javascript to encrypt sensitive information, such as encrypting passwords in plain text into ciphertext and submitting them to the business backend. However, because Mini Programs are based on H5 technology in nature, the security is not high, such as using javascript on H5 is easy to see the encryption logic, or the encrypting strength is not enough, third-party input methods listening, memory traversing, etc., will still cause problems such as password leakage.
In order to improve the ecological security of WeChat open platform, aiming at the possible security problems in Weixin Mini Program digital password input scene, WeChat has opened the security keyboard type in input component.By introducing the secure keyboard, the Mini Program can encrypt the key information in the process of user input, prevent the keyboard eavesdropping, protect the memory, and effectively protect the security of user data assets.
# Security Keyboard Protection Principles
Secure keyboards use an asymmetric decryption algorithm, which requires two keys, one called a public key, which can be made public, and the other called their private key, where they need to be held in private. Which public key encryption ciphertext, only the private key can be solved, and through the public key can not calculate the private key, so even if the hacker to get the public key can not decrypt ciphertext.We generally put the public key on the guest (such as Weixin Mini Program environment) to encrypt, and the private key on the business background, so that only the background can decrypt.Hackers are easier to hack on the local client, but the backend is much harder. Even some businesses store the private key inside the hardware encryption chip, which is a situation where hackers cannot obtain the private key, so using asymmetric cryptographic algorithm is the recommended mode for security keyboards, and security can be ensured. In order to guarantee the value of the private key, we require different Weixin Mini Program services to use their own unique public key private key pair,This can be perfect to do business encryption data isolation, business A public key encryption data, only business A own private key can be solved, business A is responsible for protecting their own unique private key. To prove that a public key belongs to business A, we issue a numeric certificate to the developer of business A. The digital certificate is signed by Tencent officially, guaranteeing reliability and immutability. A public key is attached to the digital certificate. The private key of the business is generated during the process of applying for a digital certificate from Tencent.Businesses are responsible for managing their own private keys, and in this process, Tencent has access only to public keys, not to the business's own private encryption, which means that even Tencent cannot decrypt the passwords entered by users of the Weixin Mini Program business.In order to meet the requirements of national compliance, we have issued a numeric certificate for the domestic cryptographic algorithm, which means that the asymmetric encryption and decryption algorithm uses the sm2 algorithm, rather than the international algorithm such as rsa.
Different Weixin Mini Program services, the format of the data that may be encrypted may have different requirements,For example, when the user enters the password "123456," some businesses can encrypt the text directly, and some businesses may want to do a hash processing before encrypting, such as using md5 ("123456"). After making the hash, It can more effectively protect the user's plaintext password, making it difficult for businesses to speculate about the actual password of the user. Other businesses may use the sha1 hash algorithm sha1 ("123456"), and others may use the more compliant domestic password hash Algorithm sm3 ("123456"). Even some businesses want to add some confusion characters (called salts in cryptography) to the password text for better protection, which might be turned into sm3 ("123456 + abc"), where "+abc" is an example of the additional confusion character. Therefore, in order to allow different Weixin Mini Program services to meet their own business needs of the encryption format, the Mini Program security keyboard also opens the ability to configure the password format. To better align with your overall business, however, this format is not universally compatible, so when you apply the Mini Program security keyboard, it may involve some retrofitting of the backend security service, so evaluate the feasibility in advance.
# Use Procedure
# 1 Generate a certificate signing request
Developers can generate their own public and private keys, certificate signing requests, and can also generate certificate signing requests through tools provided on the WeChat side.Tools available via WeChat ( Windows / Mac )The steps to generate a certificate signing request are as follows:
- Generate public and private keys with SM2GenerateKeyPair function
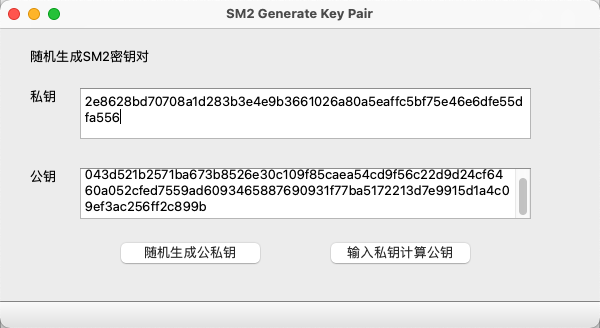
- Generate CSR with the SMGenerateCert CSR function
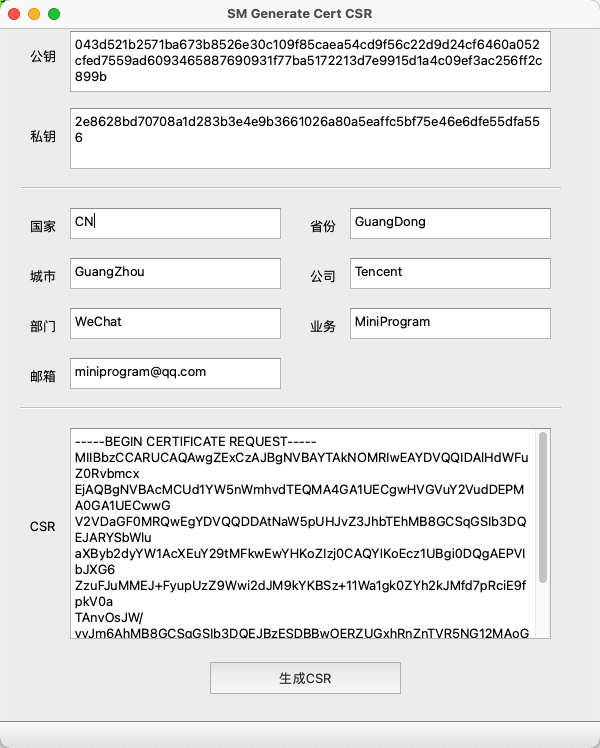
# 2 Generate Certificates
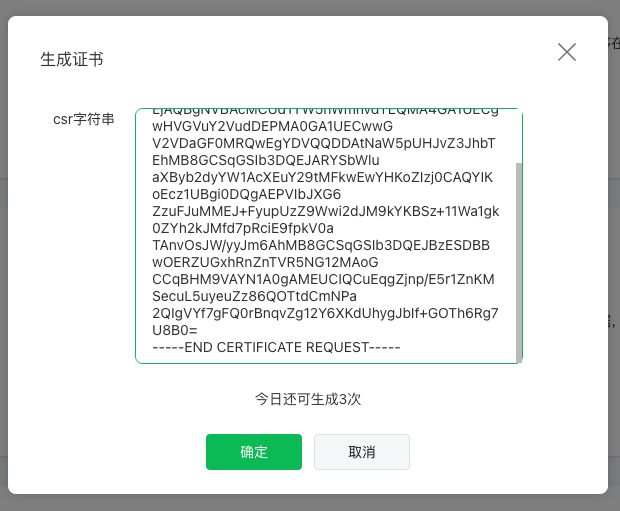
In the Weixin Mini Program management background "development" - "development management" - "development settings" - "security keyboard certificate" section fill in the CSR to generate.
# 3 Use of Certificates
- Place the generated certificate in the Weixin Mini Program code package.
- Set type = "safe-password" in the input component, and set the associated parameter (safe-password-cert-path、safe-password-time-stamp、safe-password-length、safe-password-nonce、safe-password-salt、safe-password-custom-hash)。
# Code examples
<input
style="border: 1px solid blue;"
type="safe-password"
placeholder="123456"
safe-password-cert-path="/minipro_test_cert.crt"
safe-password-time-stamp="1618390369"
safe-password-nonce="1618390369"
safe-password-salt="zefengwang"
safe-password-custom-hash="md5(sha1('foo' + sha256(sm3(password + 'bar'))))"
bind:blur="onBlur"
bind:input="onInput"
value="{{value}}"
></input>
<button bind:tap="onClear">clear</button>
<view>{{detail}}</view>
Page({
data: {
value: '123'
},
onInput(res) {
console.log('onInput', res)
this.setData({
value: res.detail.value,
})
},
onClear() {
this.setData({
value: '',
})
},
onConfirm() {
console.log('confirm')
},
onBlur(res) {
console.log('onBlur', res)
this.setData({
detail: JSON.stringify(res.detail, null, 2)
})
},
})
# coded text
# Secret text format
In order to protect the user password, a variety of cryptographic algorithms are used to protect the user's sensitive information.These algorithms can be configured flexibly according to the actual needs of the Weixin Mini Program business, because different Mini Programs use different password encryption formats, so it is necessary to configure them to suit your business.
Weixin Mini Program The general format of the password encrypted by the secure keyboard is as follows:
'V02_' + sm2(header + timestamp + '\0' + pbkdf_hmac_hex(password, salt) + '\0' + nonce + '\0' + 随机数)
Where pbkdf_hmac_hex () evaluates the algorithmic expression for the hash for the secure keyboard, which can be set by the safe-password-custom-hash property. The first two bytes of the header identify the password hash algorithm:
- 0x00 0x00: custom hash
- 0x00 0x07: pbkdf_hmac_hex
This format takes several security considerations into account:
- Anti-replay: pass in the correct timestamp timestamp, each encryption nonce to maintain self-increment, to ensure that even if the password is the same, each encryption ciphertext is not the same
- Bulls-proof: sm2 asymmetric algorithm itself guarantees the possibility of a Bulls-proof hack
- Anti-traceability original: built-in pbkdf_hmac_hex algorithm, you can also customize the hash algorithm;
- Prevent rainbow table attacks: Weixin Mini Program developers can customize dynamic salt;
Weixin Mini Program Developers who want to use a secure keyboard, first locally generate sm2 key pairs, and then go to the Mini Program management background to apply for a Mini Program secure keyboard numeric certificate. After the certificate is issued, it needs to be released along with the Mini Program code. Weixin Mini Program When calling the secure keypad, it is necessary to pass in the number certificate of the secure keypad of the Mini Program. After the validity of the certificate is verified, the public key of the certificate is extracted and the user data is encrypted with sm2 arithmetic. Because uses the certificate public key encryption, only then uses the developer own to hold the private key to be possible to decrypt the data plain text. During network transmissions, even if the ciphertext is maliciously intercepted, the attacker cannot get the plaintext.
# How to decrypt or verify the secret
'V02_' + sm2(header + timestamp + '\0' + hash(password, salt) + '\0' + nonce + '\0' + 随机数)
After the background receives the ciphertext, parse it by reference to the above format: 1、 Remove the cipher 4 byte prefix; 2、 Using the sm2 private key corresponding to Weixin Mini Program security keyboard certificate to decrypt, get the plaintext data; 3、 Parsing plaintext data, you can get the time stamp, password hash, nonce and other fields;
First of all, Weixin Mini Program developer background can only get desensitized password hash, can not get plaintext.Of course, in accordance with compliance requirements, the background should not be able to obtain the plain text of the user's password. Secondly, Weixin Mini Program developer background should properly save the password hash, as the basis for matching user passwords are consistent.For example, in the registration or password change process, after the backend SM2 private key decrypts the password hash, it should be persisted in the database (or other storage technology). In the subsequent user login or other password verification scenarios, by comparing the password hash requested by the user and the previous saved password hash is consistent to determine whether the password is verified.